Hello Guys, today I am going to show you The huge Description About Most dangerous virus in modern age I.e. Ransomware. In This article, I will show you what is Ransomware virus?, How many Types of Ransomware?, Who Are Involved In this Attacking? How Does it Spread in Our Computer System?, How Does Ransomware Get onto a Computer? Ransomware Virus List and Their Information, What Can Be Done to Prevent This Virus From My Computer?, What You Do If Your Computer Has Already Been Targeted and trick to Get your data back without Paying the Ransomware hacker. so just read on…..hope This will definitely help you to get rid of this dangerous problem.
What is RansomWare? [Full Review]

Ransomware is a kind of malicious software that carries out the cryptoviral extortion attack from cryptovirology that blocks access to data until a encrypts them, obliges that you pay to get your files back. Simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse. More advanced malware encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. The ransomware may also encrypt the computer’s Master File Table or the entire hard drive. Ransomware attacks are typically carried out using a Trojan that has a payload covered as a legitimate file.
It is so difficult to think, but the first ransomware in history emerged in 1989 (that’s 27 years ago). It was called the AIDS Trojan.
How many Types of Ransomware?
There are two types of ransomware in circulation which is given below.
- First one is Encryptors, which incorporates advanced encryption algorithms. Examples include CryptoLocker, Locky, CrytpoWall and more.
- The second one is Lockers, which locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. Examples include the police-themed ransomware or Winlocker.
Who Are Involved In this Attacking?
While initially popular in Russia, the use of ransomware scams has grown internationally. Three days ago Probably Russian and Korean countries hackers are hacked more than 90 countries computers. This news correct are not but it’s guessed by the experts that those countries hackers are involved in this hacking method. Our hands are clean we are not targeted any of those countries but by saying news report by the experts. Wide-ranging attacks involving encryption-based ransomware began to increase through Trojans such as CryptoLocker.
How Does it Spread in Our Computer System?
It is reported by the USCRT, ransomware grows easily when it attacks antiquated software. The best experts say that WannaCry is spread by an internet worm — software that spreads copies of itself by hacking into other computers on a network, rather than the usual case of prompting unsuspecting users to open attachments.
How Does Ransomware Get onto a Computer?
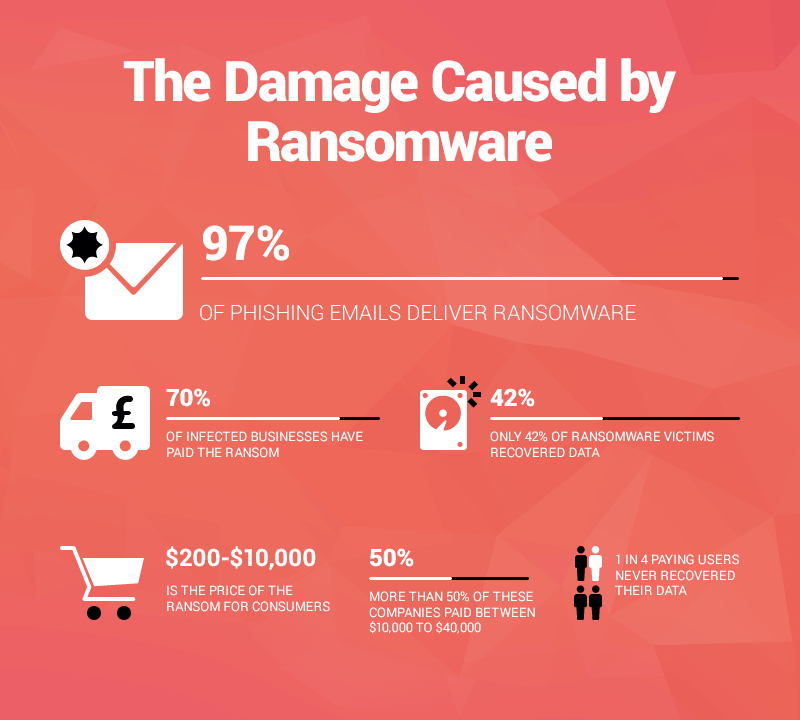
The most common ways in which Ransomware Trojans are installed are Via phishing emails
As a result of visiting a website that contains a malicious program. After the Trojan virus has been installed, it will either encrypt information that’s stored on the victim’s computer or block the computer from running normally. In most cases, the Ransom message will appear when the user restarts their computer after the infection has taken effect.
Ransomware Virus List and Their Information:-
- Reveton
- CryptoLocker
- CryptoLocker.F and TorrentLocker
- CryptoWall
- Fusob
- WannaCry
It is reported by the USCRT, ransomware grows easily when it attacks antiquated software. The best experts say that WannaCry is spread by an internet worm — software that spreads copies of itself by hacking into other computers on a network, rather than the usual case of prompting unsuspecting users to open attachments.
What Can Be Done to Prevent This Virus From My Computer?
The best way to guard your computer is to perform regular backups of your files. The malware only affects files that exist on the computer. If you have created a total backup and your machine is affected with ransomware, you can reset your machine, to begin with, a clean slate, reinstall the software and restore your files from the backup. According to Microsoft’s Malware Protection Centre, other precautions include regularly updating your anti-virus program; enabling pop-up blockers; updating all software periodically; ensure the smart screen is turned on, which helps distinguish related phishing and malware websites; avoid opening accessories that may appear different.

Here’s What You Do If Your Computer Has Already Been Targeted.
Over the weekend, an unprecedented global cyber attack hit more than 200,000 victims across more than 150 countries.
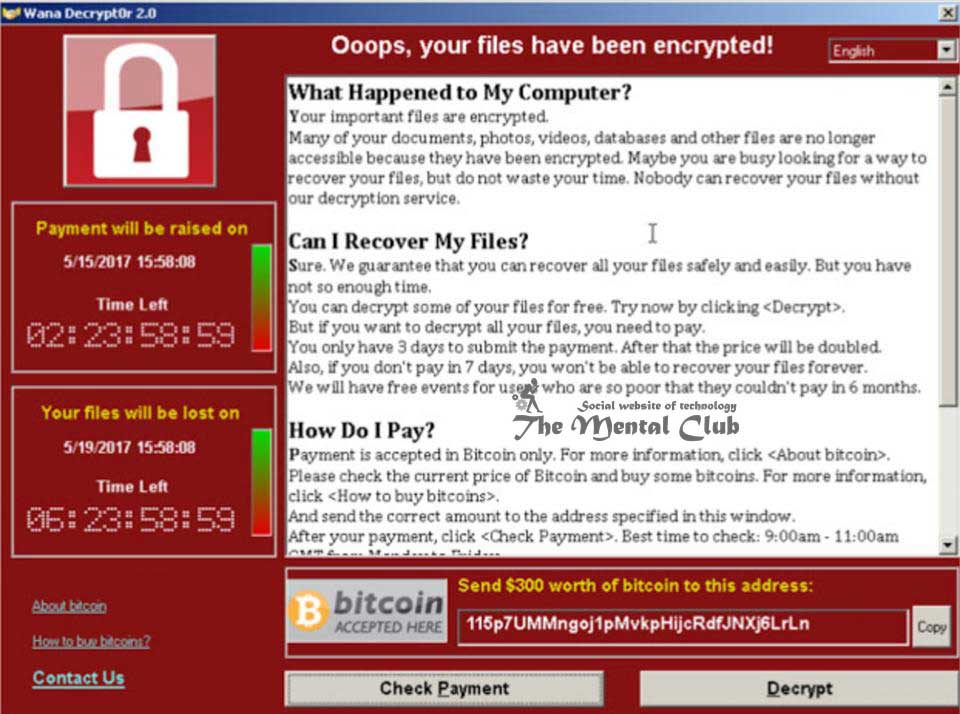
Once your computer is attacked by the Wannacry Ransomware attack, images appear on victims’ screens demanding payment of $300 (Dh1101) in the virtual currency Bitcoin, saying: “Ooops, your files have been encrypted!” Payment is demanded within three days or the price is doubled, and if none is received within seven days the locked files will be deleted, according to the screen message.
One of the first things to do today is updating your Windows software as soon as you log into your computer because that’s where the vulnerability is.
Below are the measures you can follow to secure your laptops:
1. Avoid visiting unknown websites
2. Avoid downloading any files from the unknown websites
3. Abstain from opening or sparing of connections gotten through obscure messages. Despite the fact that an email gotten from a known individual, please tap on the sender’s email address to verify the actual email id of the email received before opening any attachment. This is to make sure that the email received is not a spoofed email.
4. Take a reinforcement of your PC/tablet regularly which is an ideal approach to maintaining a strategic distance from information misfortune at the season of malware assault.
5. On the off chance that you speculate your PC/tablet is contaminated, promptly separate the gadget from the system to maintain a strategic distance from it spreading to different gadgets and educate your IT bolster group.
However, in the event that you are heartbreaking and the ransomware is as of now introduced on your machine today, there is not much you can do. Once you are affected, you have to go for a complete wipe and restore with the backup you hopefully have created.
How to Get your Data Back Without Paying the Ransom?
Their several sorts of ransomware out there, yet digital security scientists are working all day and all night to break the encryption that in any event some of them utilize. Lamentably, the most famous families have turned out to be unbreakable up until this point. In spite of this, there are many other crypto wars strains that are not that well coded and which specialists were able to crack.
To help you discover an answer for recuperating your information without further financing ransomware makers, we put together a sizeable list of ransomware decryption tools which you can use.
We prescribe you perused about how these apparatuses function heretofore so that you’re certain this is the best answer for your case.
Do remember that decryptors could wind up noticeably out of date due to consistent updates and new, enhanced versions released by cyber criminals. It’s a never-ending battle, which is why we urge you to focus on prevention and having multiple backups for your data.