Understanding Malware vs VIRUS vs SPYWARE vs ADWARE vs WORM | What’s the Difference
You could understand that if you make a wrong move on the Internet then how it may be in danger and after knowing you would break down in fear. The Internet is not so simpler as we see it in a normal way. Because the danger is hidden in every step. For example, when you download more or less data from the unverified website then you have noticed that some data can be downloaded for free or you download another file instead of your desired file. If you do not believe then you watch that while downloading Firefox Flash Player then you watch that automatically download McAfee Security Scan Plus. We face these kinds of problems either lack of awareness or for hurrying. Because so many previous checked download button do stay in a one download page. So, as a result, the automatic download has been starting. As a result, hackers are getting a chance to attack you. These are called threats. all threats are not the same. So, we have to know all about these types of threats.
Complete Differences Between Malware vs VIRUS vs SPYWARE vs ADWARE vs WORM
Now the questions are : What is Malware? What is Virus, Spyware, Adware, Worm? How does it work?
What is Malware?
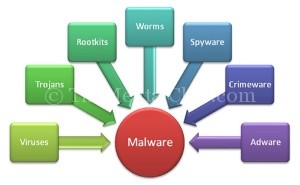
Malware is a shorten version of the Malicious software. We, the most computer users, which we think as a virus, is nothing but a malware. There are so many forms of malicious software such as the virus, warm, trojan, spyware etc. generally, malware are called those programs which is harmed to others.In below, we are discussing the various kinds of malware.
Top 10 Devastating Computer Viruses Until Today
Luckily our internet security or web browsing are continuously searching this malware. Now, the question is what should I do if our PC is attacked by malware? For getting answers we welcome to our tune. We will know the various kinds of malware, their works, and their bad and harmful effects and its remedies.
Computer Virus: A Security Panic
The virus is made from the combination of some harmful codes which do their job after installing this coded software. If a computer is attacked by virus then it scatters in all computers and makes disable the operating system and all files of your computer.
If your computer is attacked by virus then it is very difficult to find out iots own position. Because I have told that it can create its own image and scatters itself. It also transferred in another computer if the computer is attached with your virus affected computer. Like Malware, the main aim of the virus is that to disable your Operating System. Except for some virus, most of the virus can damage your computer. According to Experts, MAC and LINUX based Operating System is not affected by the virus.
Adware: Advertising-Supported Software
Now, we are discussing the malware which is the most threatful virus. Adware is the collection of software or applications which come in your computer unknowingly. Generally, during downloading any files we download one instead of others unknowingly. Fort this, adware button has checked before adware downloading and on that download page, there are so many download button. Just one click in wrongly, the Adware will be downloaded automatically.
Adware Infection is not only our own mistake. If the device maker institution has added adware then, there is nothing to do it. If Lenovo and Superfish cause exception, then what should we do?
Trojans and Backdoors
Trojan Malware has been named to the trojan horse. Trojan Horse is for those who do not know about this. You may know the story of the historic battle of Troy and trojans. When it comes to the attacks Trojans Troy City of Troy, the Trojans cut through the wall of the city were not able to enter. They cleverly hid their warships to the sea builds a huge wooden horse. Heroes were hiding inside the Trojan. When he realized that the city of Troy and the Trojans run away, he could see the sea in a wooden horse large. He considered it a blessing of the gods, brought into the city of Troy. Then the soldiers of the Trojan horse broke out of the darkness came and the castle doors open from the inside out on the road to break into the inner senabahinila Trojans . Thus , despite the strong wall of Troy City of Byron unprotected destroyed.
Trojan virus has become inextricably linked with the history of the Trojan Horse. It just works Trojan virus. Heed it into your computer and then trying to establish contact with the server behind the scenes. When successful, then open your PC to control the backdoor. This means that hackers can control your PC from a distance and they stole the secret things.
However, if you can understand that after being infected by a Trojan virus has infected your PC , then all the great advantage that if you turn off the internet connection to control your PC or in any way a hacker cannot steal information . Close connections with the Trojan virus remover you can easily remove the Trojan can .
Spyware: Your Hidden Enemy
With the name “Spyware” we get some knowledge about its work. Though most of the spyware is not so harmful. But, some spyware is really very harmful. Spyware mainly surveillance on internet surfing and attached with unrelated matters. Spyware, frequently, is more harmful than the trozan horse when it sends the information, banking information, pictures, emails etc of your computer to another users.
Spyware mainly comes to your computer during the downloading of computer software, freeware, shareware etc. Though spyware is mainly used in add surfing but you must be little careful and keep yourself safe.
Scareware and Ransomware: The New Weapons of Cheating
Though the ambition of Scareware and Ransomware is same their working process is separate. They both use their plot and will be forcing you to spend money on them.
What is Ransomware? How Do You Get Rid From Ransomware Virus
- Scareware is a program which is installed in your PC unknowingly during the net surfing. And Malware will tell you by alerting that yor computer is attacted by malware and for removing this you have to buy this full version of the software. I sometimes have trouble reading this, you should tell this tune.
- Ransomware works in a different way. It locks all of your important files and your PC and demands money when you want to unlock your PC. Though it is not difficult to remove it but the new experience computer users do not aware of this.
Worms: the Most Devastating Malware
Worms is the most devastating malware. If any file of worms attached system is transferred to another computer through internet then creates security fault in the networks and also in that computer. As a result, all networks has come under it and the attached computer is also badly affected.
From getting rid of this, the affected computer has to be separated from worms. Then, worms can no be attacked. So, be aware and make others aware about online virus itself.
How do you keep safe yourself in Online?
We have known about some threats which harm our computers during internet surfing. The Internet is the driving force of the world so we can’t stay away from the internet. We keep safe ourselves if we be a little careful and follow some below-mentioned steps.
Also Read: How to protect your family against online dangers
- You have to update your operationg system and other programs. You are requested to install a good anti-virus software and keep update itself.
- Personally, I use ESAT Smart Security and AVG Internet Security and you have to use strong firewall and be conscious from threat.
- You keep detouch yourself the program download from the unknown source.
- You have to scan the programs or softwares by your anti-virus or anti-malwares before opening it.
- You keep avoid yourself from pyrated software. You stay away yourself from the naked films and pornographic websites.
Internet is all for us. Without Internet, we can’t move forward. To keep yourself safe at all times have the right knowledge. Know yourself, not be misguided by anyone, then take the right steps. get rid of all the filth and darkness of ignorance. So, to keep yourself and do not have to worry twice.
Final Words:
If you like my tune, then please comment on my post. Your comment encourages me to write down better tune. If my tune is thought to be a unique tune, then you are requested to like my tune. So, let’s come and give up the copy-paste and encourage another tune. See you in the next post.