Today, my article is: What is Phishing and the ways of Surviving.
Phishing is such an activity; it is done in collecting the information through an electronic system in a disguise of any reliable institution.
In general, any social institutions such as banks, IT administrations and these institutions’ unauthorized websites enticed general people.
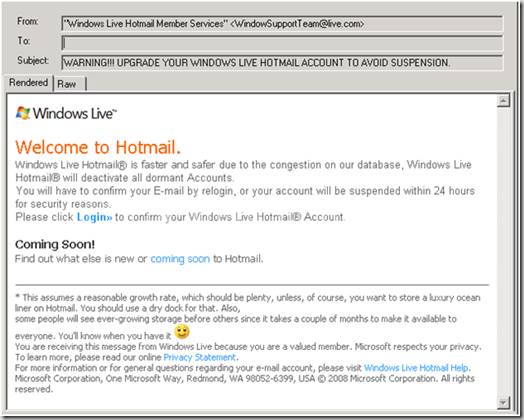
The links on Phishing site are sent through instant messaging and emails. They sent links to the emails and after clicking on this link, the user goes to the malicious website which looks link almost an official website.
They use the weak security internet system in their own way by using of Phishing process.
The amount disservice is larger than benefits in the use of Phishing process.
There are various types of Phishing process. The processes describe in below:
Phishing:
Phishing is such an activity; it is done in collecting the information through an electronic system in a disguise of any reliable institution.
Spare Phishing:
Some of the individuals or a company where they obtain information about a particular person.
Clone Phishing:
The rest of the content of any email previously sent by cloning or links to other sequence changes is sent to the e-mail addresses. It seems as though it is sent from the original address.
This mail can sent from previously attacked of any computers.
Link Manipulation:
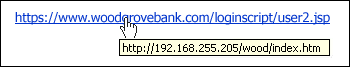
Through this, a victim can redirect in any malicious website. In general, Phisher use any wrong or different url or sub domain.
Filter Evasion:
Phishers use image link instead of text just because, as they do not catch in an anti-phishing filter.
Website Forgery:
Phishers can use Java commands instead of the address bar. It is also a photo of legit websites via the address bar. Moreover, they use more tricks. For catching these tricks you have to be more advanced.
Moreover, through flashing technology, they use flash dependent websites for deceiving anti phishing process.
Phone Phishing:
It proves that the website does not always require at all. By calling phone to your number, they entice or tempt people for telling very important information such as: ATM Card number etc.
What should be done for surviving from Phishing?
-
Please keep watching the address bar during net surfing. If your mouse pointer hovers in the address bar or you will see in where this page goes you if you keep your mouse pointer in the right corner.
- You use various kinds of software such as anti-phishing software. Firefox’s extension- (pet name), which contains the name of the first real save the page to come back on the next.
- The spam filter on email is some active. Though, it does depend on that machine.
- You do not log in by giving username and password after do not make sure. No matter if you need to login, please consult the official site.
- In Legit website, such as bank, which contain certain information in the media Facebook, which do not contain in phishers. If any message comes from legit websites, then they mention your name. For example, if any message comes from Facebook, then Facebook mentions your name such as hello xxx, not the “hi Facebook user”.
- Generally Browse the website of the attack could be for authentication of the secure website ssl, with strong PKI cryptography is used. It is used for the server authentication website URL is used as the identifier. Verify that the address of the browser address bar, and to indicate the help of padlock. Modern browser verifies addresses in the green padlock are used as a better indicator of the high level of security.























![How to Hack Any Computer By Android? [Root] How to Hack Any Computer By Android [Root]](https://thementalclub.com/wp-content/uploads/2017/09/How-to-Hack-Any-Computer-By-Android-Root-218x150.png)









